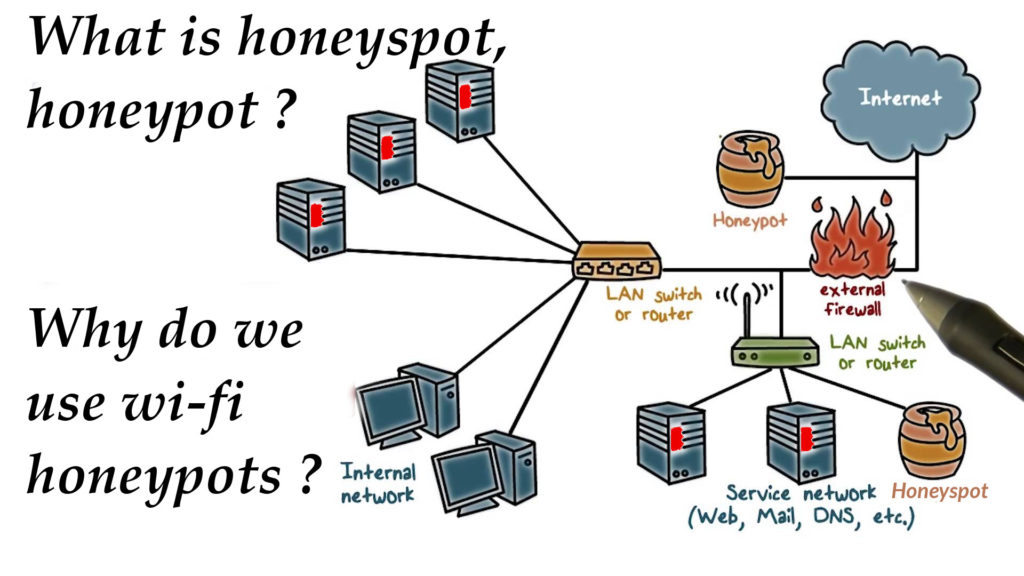
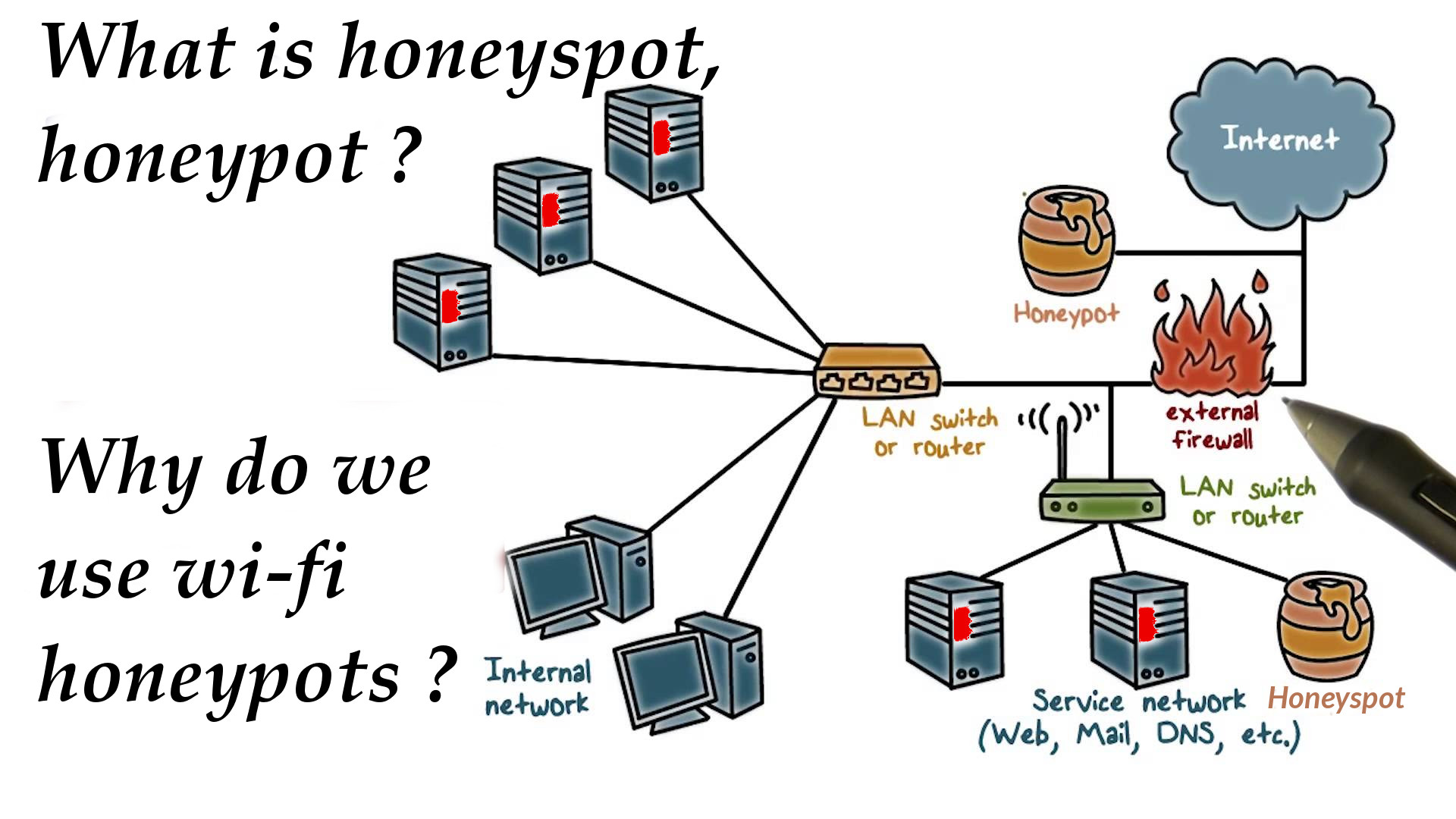
What are Wireless Honeypots?
T
here are different types of honeypot system that are commonly used as well. They are called wireless honeypots. Getting a wireless honeypot deployed in a network is mainly used for the sake of capturing the behavior of a system which resides inside a wireless network. Information and statistics about such behavior and activities could be easily gathered from such honeypots. Wireless connections contain both the technology of IEEE 802.11 and some other similar technologies like Bluetooth for instance.Why do we use Wi-Fi honeypots?
We are basically into using Wi-Fi honeypots to track any malicious activity on the target network. To elaborate more, using some access points, a wired network, and some open-to-attack computers could simply lead to obtaining a Wi-Fi structure, right? In this structure, Wi-Fi networks are really vulnerable to enormous amounts of attacks, which urges the need for a Wi-Fi honeypot that could simple be capable of getting any unauthorized traffic captured and getting some questions answered about the possibility of catching wardriving and hackers which are collecting their forces to attack a wireless network and get it compromised.
What is Honeyspot?
Honeyspot is, in fact, the name of a wireless honeypot project which got the original support from Honeynet, the Spanish project. This project is in fact considered to be the most famous honeypot projects when it comes to wireless honeypots. The reason why it has this strange name lays back in the two terms Honeypot, which is the basic idea of wireless honeypots, and hotspot, which is the basic idea of a wireless network.
The rationale beyond this honeyspot project is basically to monitor an attacker while he tries to act maliciously against a wireless network to know his behavior and actions. The traffic going through such honeyspot is only the malicious traffic. On the other hand, since any professional and experienced attacker is capable of identifying whether it is, in fact, a real system or it is a fake honeypot, it is no different when it comes to honeyspot project where same experienced attackers could recognize and distinguish between honeyspot and real systems. The way in which a honeyspot appears matter to convince the majority of attackers that it is a real system. There should be many similarities between the real system and a honeyspot system.
All of the IP address spoofing, hacking of web session, and spoofing of a MAC address become all recognized and identified using Honeyspot project. Special approaches to get the clients of a wireless network hacked are also understandable with the help of the Honeyspot project. The result of all of this information and understandings, the existence of much more secured systems become achievable.
There is, in fact, a special network architecture that works best with the Honeyspot project.
The architecture consists of the following components:
-
- There has to be a Wi-Fi access point (WAP) to which clients can have access to and connect to it. An attacker is also able to connect to the WAP. This is the main source of internet connection for all its clients.
-
- There are on the other hand the wireless clients (WC) who seems to be utilizers of the network in the first place to gain access to the internet connection provided using WAP. However, all of these clients are not actual devices, and they can connect to the honeyspot network. If these clients are not real, then why on earth we have them in the first place? The basic answer to this question is that we mainly need to create traffic in the fake system. We want to show the attacker that there is traffic going through the wireless honeyspot as incoming and outcoming traffic. This gives the attacker a sense that he is attacking a real system, not a fake one. Consequently, he becomes tempted to attack the network through initially monitoring such traffic with the use of his monitoring tools used for the attack.
-
- There is also what is referred to as WMON which is a wireless monitor module. In this module, traffic gets captured such that any information about the network traffic could be retrieved and monitored. This assists security administrators in getting to understand the attacks and get information about it. This shows how important this module is.
-
- Another module exists, having the name of WDA which refers to wireless data analysis module. The work of this module mainly depends on the work of WMON in the first place. This module takes part with the administrators in the process of getting to analyze the captured traffic. Now you can see why this module relies heavily on the WMON module. While capturing data happens by WMON module, WDA comes to analyze and examine this traffic. The mechanism goes like the following: when WMON captures the records of traffic, it saves them and then sends them directly to WDA to make sense of this traffic through analyzing it to get important information from it.
- Finally, the last module is named WI module. This module is, in fact, a wired structure which is optional in the architecture used for honeyspot, meaning that it could exist or not in the architecture without having to worry about any problems. The idea is basically that this network structure may be designed to have a wired connection structure as well as the wireless connection. This just gives a slightly different aspect to the usual network structure used for honeyspot.
Resources:
http://www.diva-portal.org/smash/get/diva2:327476/fulltext01