Wifiphister is a wireless security tool which can be used to launch phishing attacks against targeted Wi-Fi network to gain access to a wifi network and steal credentials, infecting the network with a virus and launch DDoS Attack.
T
he method of attack that we will be using to hack wifi using WiFi-phishers it’s aHow does this tool works.
- It first jams the wireless network access point’s, in which it de-authenticate or disassociate all devices that are connected the targeted access points by sending disruptive packets towards it.
- The tool also sniffs the targeted access point settings and copy over the configuration which then
are use to generate fake access points with the same settings (Evil twin wireless network). - Its then employs a stripped-down net server which then responds with HTTPS (Hyper Text Transfer Protocol secure) in real time requesting your WiFi credentials.
Wifiphisher wireless network hacking Demo.
This Tutorial will base of Kali Linux OS, you will need to download wifiphisher from here on gitHub. Open your terminal and follow the instruction listed below.
Here is the prerequisite that WifiPhisher needs to work successfully.
- apt-get install libnl-3-dev libnl-genl-3-dev
- git clone https://github.com/wifiphisher/roguehostapd.git
- cd roguehostapd/
- python setup.py install
- git clone https://github.com/wifiphisher/wifiphisher.git
- cd
wifiphisher sudo python setup.py install- apt install wifiphisher
Hack WiFi Using Wifiphisher
Launch wifiphisher from your terminal.
:~# wifiphisher
Here we select your targeted WiFi network by using arrow keys to cycle between your options and enter to the keyboard to activate.
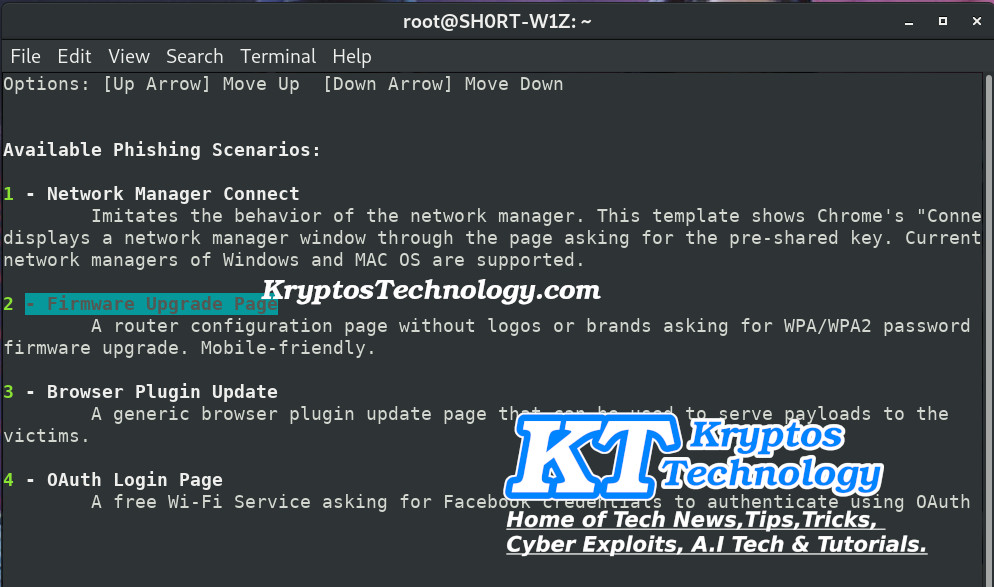
Now you need to select the attack method i strongly recommend option 2 (Firmware Upgrade Page) it’s more convincing and it won’t frustrate the user like how method option 1 (Network Manager Connect) would work.
The image below shows the fake AP that was generated by WiFiPhisher and what the victims will see.
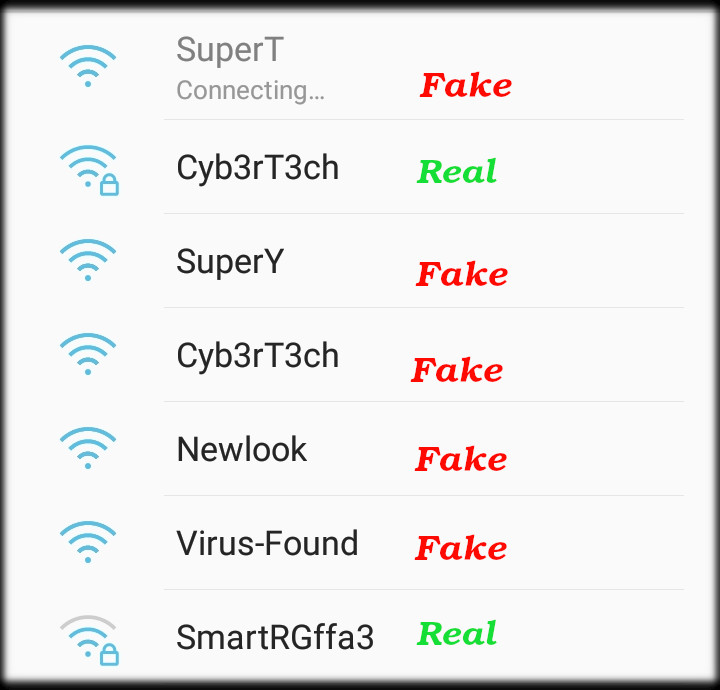
Fake WiFi Generated by WifiPhisher 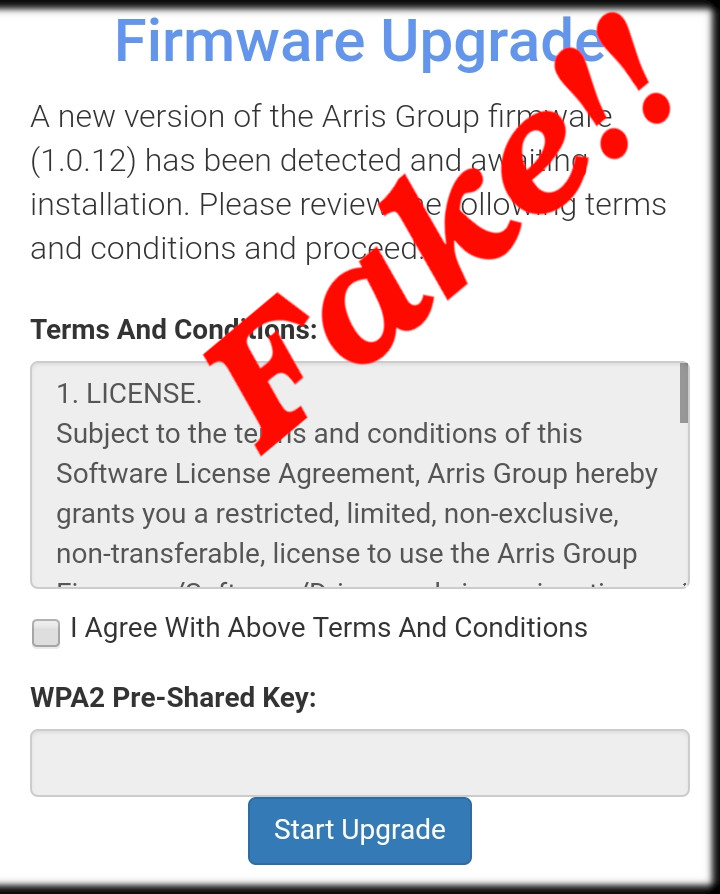
Fake Firmware upgrade to get wifi passcode
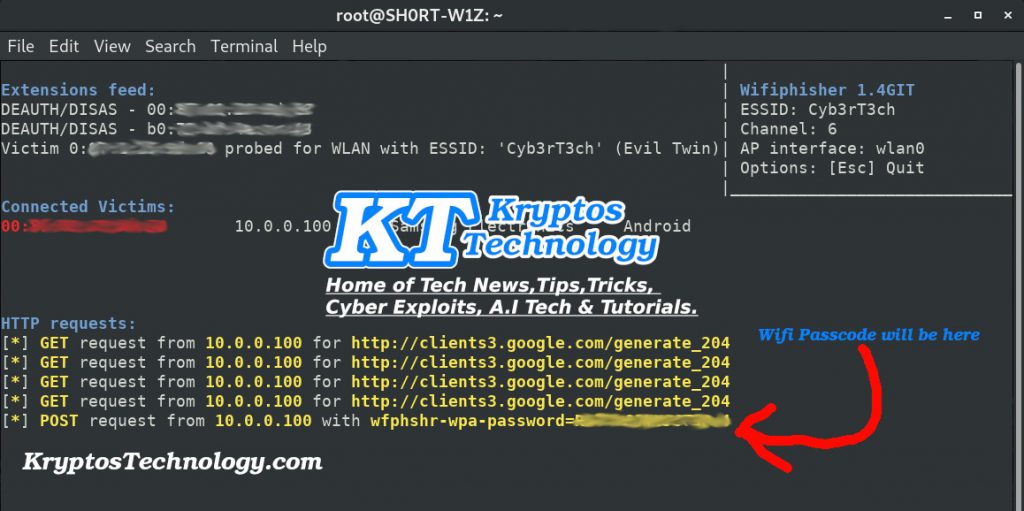
So when the victim connects to one of our fake AP (Access point) and get redirected to our Firmware upgrade page and hopefully agree to the terms & conditions, then enter their wireless passcode it will then be displayed like in the image below.
THIS IS NOT A JOKE!
MISUSE OF THIS TOOL RESULTS
IN CRIME! AND THE RESPONSIBILITY IS
ONLY YOURS.
Okay everyone let me know what you think about this article in the comment sections, this tool is not limited to just WiFi hacking, it also can be used for Facebook phishing attack with option 4 0Auth login page.