A security firm called Zscalar spotted a malicious app living on the Play Store with a false moniker System Update. It managed to survive for around 3 years. Under the hood, it hides a spare called SMSVova which can be controlled by the attacker via SMS to fetch location details and change device password.
C
onsidering the gigantic size of the Google Play store, one can easily agree that malicious apps might exist on the platform. But what’s has been known lately has a hidden surprise element.A malware, disguised as “System Update”, managed to exist on the Google Play Store for around three years since it was last updated in 2014. It might have lived for some more time if a security firm Zscaler didn’t contact Google regarding the existence of the app, hiding a spyware called SMSVova.
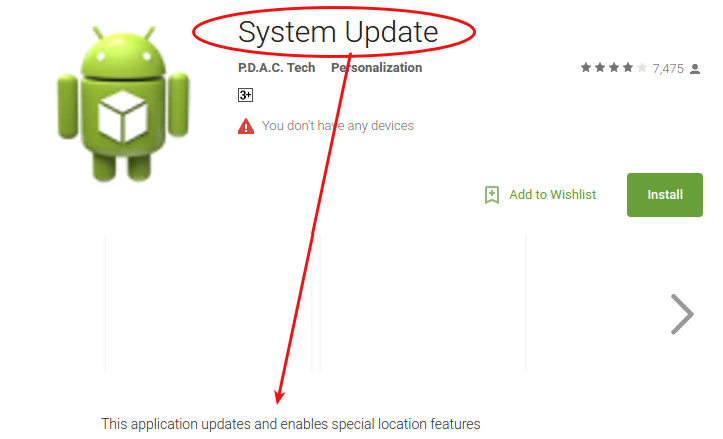
“The application updates and enables special location features,” reads the description on the app’s page which itself looked rather dubious, featuring blank white screenshots. Still, the app had a download count between one and five million.
People who downloaded the app posted reviews stating that the app didn’t update their system and their device froze after the installation.
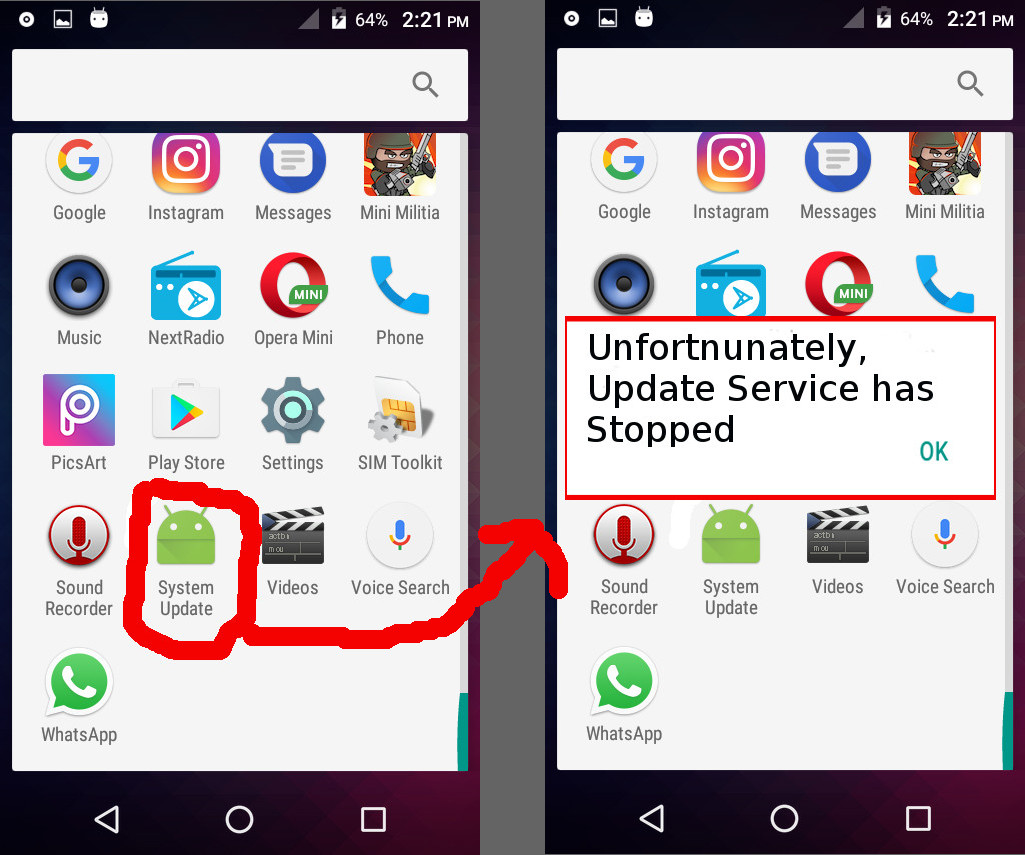
In the blog post, Zscaler’s Shivang Desai described the working of the app. When launched, the app displays an error message saying the update service has stopped. It continues to do its job in the background.
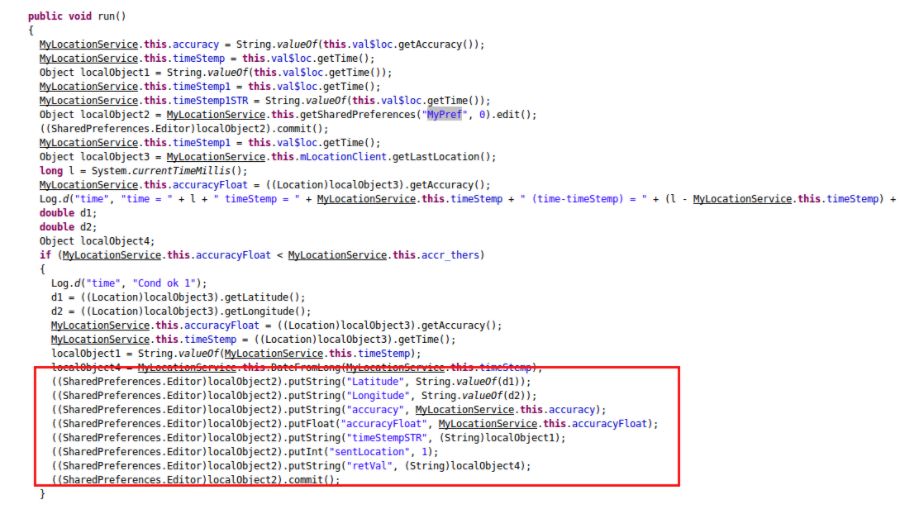
The spyware creates an Android service called MyLocationService to fetch the last known location and stores it in the Shared Preferences, a place where Android stores an application’s data.
Additionally, the spyware scans for incoming SMS texts having more than 23 characters in length and containing the string called “vova-“. It also scans for a string called “get faq” in the SMS.
If the attacker sends an SMS including the command ‘get faq’, he’ll receive a response including the list of commands he can execute on the device by sending further SMS. This includes changing the password of the device.
In case, the device’s battery is low the spyware would send the last known location to the attacker, according to Desai. However, he’s unclear about the purpose of the location recording.
Desai noted that the SMS-based behavior of the app might’ve helped it get past Google’s filters and remain undetected from anti-virus tools.
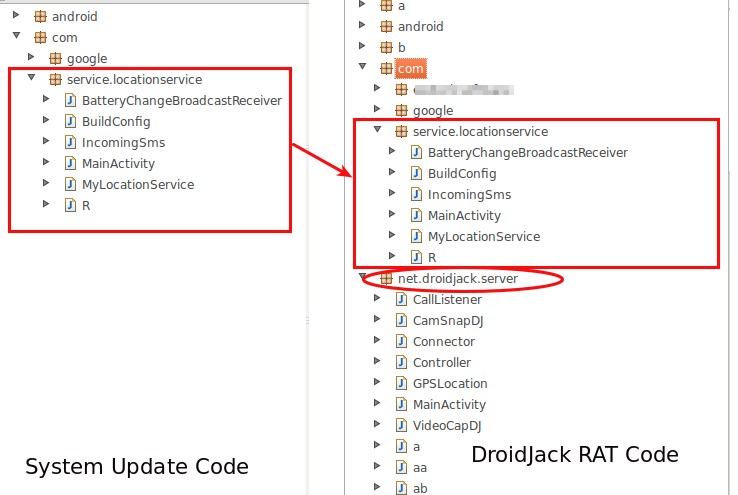
Also, SMSNova’s code has a striking resemblance with that of a widely-known remote access trojan called DroidHack RAT. It might be possible that the spyware might be an initial version of the trojan.