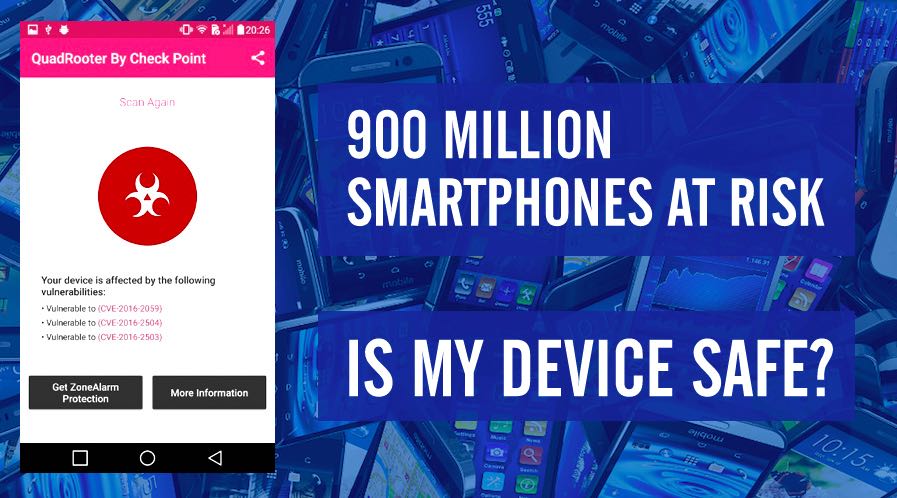
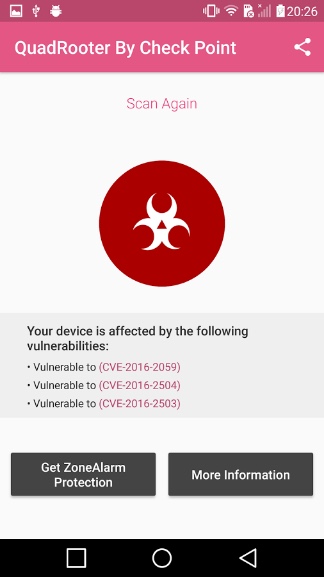
A set of four vulnerabilities, known as Quadrooter, can be exploited to gain access to around 900 million Qualcomm processor-based Android smartphones. The security firm Check Point has brought the vulnerabilities to light.
Called the Quadrooter, these are capable of gaining access to 900 million Android devices around the world. It’s expected that the bug will target devices running on Qualcomm’s processors.
The Quadrooter bugs:
- CVE-2016-2503 – Qualcomm GPU driver bug.
- CVE-2016-2504 – Qualcomm GPU driver bug.
- CVE-2016-2509 – Qualcomm kernel module bug.
- CVE-2016-5340 – Qualcomm GPU driver bug.
Three of the above flaws have been fixed. One left, for which Qualcomm has released the code, is expected to be fixed by September. These patches have been made available for the Nexus devices as a part of Google’s monthly security updates. Users of other devices will have to wait till their manufacturers make the patch updates compatible with the devices.
Here is the list of devices at risk:
- Samsung Galaxy S7 and Samsung S7 Edge
- Sony Xperia Z Ultra
- OnePlus One, OnePlus 2 and OnePlus 3
- Google Nexus 5X, Nexus 6 and Nexus 6P
- Blackphone 1 and Blackphone 2
- HTC One, HTC M9 and HTC 10
- LG G4, LG G5, and LG V10
- New Moto X by Motorola
- BlackBerry Priv
These bugs allow a potential attacker to gain root privileges allowing full device control by exploiting the vulnerabilities. This can be done by writing a malicious app and getting it installed on the users’ smartphone. “Such an app would require no special permissions to take advantage of these vulnerabilities, alleviate any suspicion users may have when installing,” the researchers said.
Check if your device is safe from Quadrooter?
Check Point has released a free app to check whether your device has been patched for the bugs or not. You can download the app from Google Play store.
Qualcomm is a pioneer in the smartphone SoC (System on Chip) business with the highest market share in the world. Their Snapdragon line of SoCs has been adopted by major brands, you can see the list of vulnerable devices above. The revelation of major bugs in Qualcomm’s chip put millions of devices at risk.
“Qualcomm has a significant position in the development chain, in that a phone maker isn’t taking the Android open-source code directly from Google, they’re actually taking it from Qualcomm,” said Michael Shaulov, Mobility Product Management Head at Check Point.
“No-one at this point has a device that’s fully secure. That basically relates to the fact that there is some kind of issue of who fixes what between Qualcomm and Google.”
It is a matter of concern that inconsistencies in the update and patching process of Android phones are disorganized and often released without any schedule. The existence of different manufacturers in the market makes the issue even worse. The result is that the Android ecosystem has to pay for the irregularities in the patching process.