kryptos-bytes: If you don’t know about Mr. Robot, then you are living in a world full of Illusions. Mr. Robot is an American drama–thriller television series created by Sam Esmail. It stars Rami Malek as Elliot Alderson, a cybersecurity engineer and hacker who suffers from social anxiety disorder and clinical depression.
Alderson is recruited by an insurrectionary anarchist known as “Mr. Robot”, played by Christian Slater, to join a group of hacktivists. The group aims to cancel all debts by attacking the large corporation E Corp. This show takes technical realism to levels unprecedented for Hollywood. Without further ado, here are five information security lessons from season 1 of Mr. Robot.
1 – A Hacker can compromise your phone in seconds, and you’ll never even know it:
Hackers don’t need to steal your phone — that would be too obvious, and would only give them access to your data from the past.
Instead, they can gain control of your phone using spyware. They can do this in minutes, and you’ll never even know.
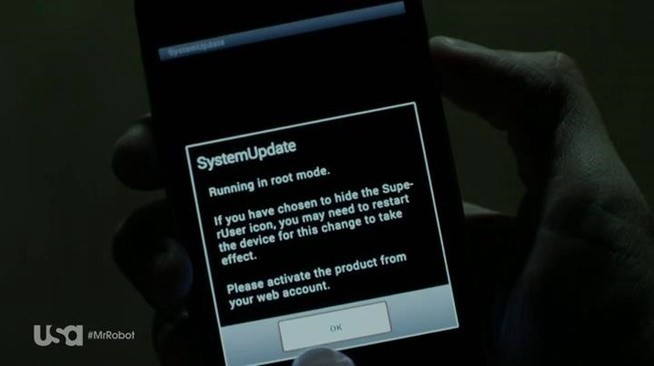 In Mr. Robot, one of the characters (Tyrell Wellick) installs a root kit on someone’s phone in less time than it takes to shower. Using Flexispy — a widely-used Android spyware tool — the character “roots” the phone — putting it in superuser mode — and then hides the normal superuser icon to obscure the fact that the phone has been tampered with.
In Mr. Robot, one of the characters (Tyrell Wellick) installs a root kit on someone’s phone in less time than it takes to shower. Using Flexispy — a widely-used Android spyware tool — the character “roots” the phone — putting it in superuser mode — and then hides the normal superuser icon to obscure the fact that the phone has been tampered with.
From now on, Tyrell is able to monitor all of that phone’s digital and audio communications.
2 – Don’t Accept CD or USB drives from strangers:
Emerging from the subway, a boombox-blasting rapper offers you a free copy of his newest album.
Now, you wouldn’t take candy from some guy in bellbottom jeans and stick it in your mouth. Don’t take a CD from some guy in a flat-bill cap and stick it in your computer!
To be fair, you would still need to execute a file. In Mr. Robot, hackers use an alluring filename like “Free iTunes Gift Card.exe” to dupe the victim into double-clicking it. This installs a Remote Access Trojan (RAT), effectively giving the attacker access to files and even webcams. Creepy.
3 – Hide Things in Plain Sight:
Sometimes the best place to hide things is right out in the open. Who would think twice about that binder of old rock albums on your floor?
What looks like a normal CD — that even plays their album scrawled on it with a sharpie—actually contains an extra layer of data stashed within. Elliot uses DeepSound app to encrypt data inside MP3 files.
Removed from any network access, the only way to read the data on these CDs would be to physically enter the premise and get a hold of them. You’d then for at least long enough to spin up an optical drive, decrypt the data and dump their contents.
4 – If you aren’t using Bluetooth, then Turn It Off:
If an attacker discovers an open bluetooth connection on your device, they could connect their own keyboard to it and start inputing commands.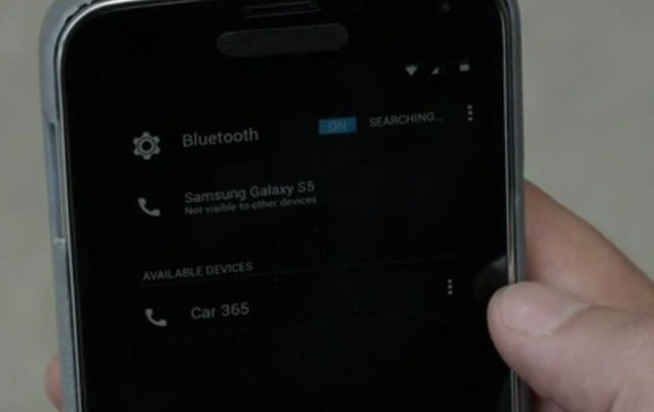
Yes, it is possible to open up a terminal with a series of hotkeys in both Windows and OS X, and from there type in malicious commands. As a bonus, turning off Bluetooth when you’re out and about will reduce your battery consumption.
5 – You are your own greatest vulnerability:
Do you know where the weakest link in any Security System is? It’s you, with your shitty passwords and how you share every part of your life online from Geo-tagging everything you do, to a photo you post of your new ATM Card.
Throughout Mr. Robot, the most common exploit is good old social engineering — manipulating people into doing what you want.
Here are some red flags to look out for when interacting with strangers:
1 – A phone call that jumps straight into “I just need to ask you some security questions first” — many services use the same security questions, and these could also be used to speed up a brute-force attempt to guess your password.
2 –A stranger approaches you with an all-too-plausible story and asks to use your phone — this is an easy way to get your phone number or other identifying information.
3 – Your own vanity, laziness, love of family, or fear of germs — these are all vulnerabilities that an attacker can take advantage of. If a stranger seems to be winding you up emotionally for no reason, they may be more than just a mean person. They may be an attacker.
That’s it for now. I hope you like the article(which I am sure you will if you are a Mr. Robot fan).

