 AceDeceiver, the malware that attacks iPhones via Apple DRM
AceDeceiver, the malware that attacks iPhones via Apple DRM
2016 seems to be a year of Apple malware. Recently we had the first ever ransomware targeting Mac users and now we have a new malware which targets non jailbroken iPhones.
The new iOS malware dubbed as “AceDeceiver” was discovered by security firm Palo Alto Networks, which said it is targeting non-jailbroken iDevices via a flaw in Apple’s DRM mechanism. The researchers said that AceDeceiver manages to get on to devices without having to clone or forge any certification processes.
“What makes AceDeceiver different from previous iOS malware is that instead of abusing enterprise certificates as some iOS malware has over the past two years, AceDeceiver manages to install itself without any enterprise certificate at all,” Palo Alto says in a blog post.
AceDeceiver works by abusing a design flaw in Apple’s DRM protection mechanism called FairPlay via a technique called “FairPlay Man-in-the-Middle”, enabling attackers to install malicious apps on iOS devices while bypassing Apple’s baked-in security measures.
Once it infects the non-jailbroken iPhone, it starts installing malicious Apps without the iPhone owners knowledge. The only thing that can give away the malware is tell-tale signs of newly installed unknown App icon showing on an iPhones’ home screen.
Palo Alto researchers stated that hackers have been using the Apple DRM exploit since 2013 but this is the first time that it’s been exploited to spread malware.
“In the FairPlay MITM attack, attackers purchase an app from App Store then intercept and save the authorization code. They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by victim,” the security firm explains.
“Therefore, the user can install apps they never actually paid for, and the creator of the software can install potentially malicious apps without the user’s knowledge.”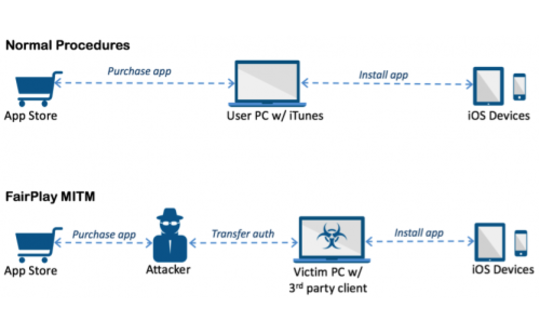
Three different iOS apps in the AceDeceiver family were uploaded to Apple’s App Store between July 2015 and February 2016, and all of them claimed to be innocent wallpaper apps. Apple’s security team removed all the three Apps in February 2016. However, the researchers note that the malware would soon be back given its track record at bypassing Apple’s vigilant security checks.
There’s no need to panic just yet, though, as Palo Alto notes that, for now at least, AceDeceiver is only targeting users in China.
Palo Alto networks has notified Apple of the malware threat, but it has yet to be patched.
