
Many people believe that they are much less likely to be bothered by malware if they use a Mac computer, but is it really true? Unfortunately, No.
A
ccording to theMcAfee Labs, malware attacks on Apple’s Mac computers were up 744% in 2016, and its researchers have discovered nearly 460,000 Mac malware samples, which is still just a small part of overall Mac malware out in the wild.Today, Malware Research team at CheckPoint have
a new piece of fully-undetectable Mac malware, which according to them, affects all versions of Mac OS X, has zero detections on VirusTotal and is “signed with a valid developer certificate (authenticated by Apple).”
Dubbed DOK, the malware is being distributed via a coordinated email phishing campaign and, according to the researchers, is the first major scale malware to target macOS users.
The malware has been designed to gain administrative privileges and install a new root certificate on the target system, which allows attackers to intercept and gain complete access to all victim communication, including SSL encrypted traffic.
Just almost three months ago, Malwarebytes researchers also discovered a rare piece of Mac-based espionage malware, dubbed Fruitfly, that was used to spy on biomedical research center computers and remained undetected for years.
Here’s How the DOK Malware Works:
The malware is distributed via a phishing email masquerading as a message regarding supposed inconsistencies in their tax returns, tricking the victims into running an attached malicious .zip file, which contains the malware.
Since the malware author is using a valid developer certificate signed by Apple, the malware easily bypasses Gatekeeper — an inbuilt security feature of the macOS operating system by Apple. Interestingly, the DOK malware is also undetectable in almost all antivirus products.
Once installed, the malware copies itself to the /Users/Shared/ folder and then add to “loginItem” in order to make itself persistent, allowing it to execute automatically every time the system reboots, until it finishes to install its payload.
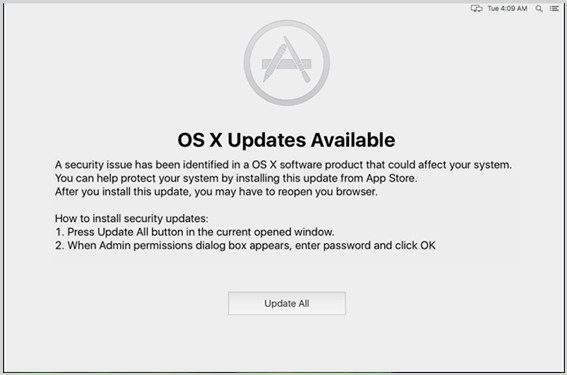
The malware then creates a window on top of all other windows, displaying a message claiming that a security issue has been identified in the operating system and an update is available, for which the user has to enter his/her password.
Once the victim installed the update, the malware gains administrator privileges on the victim’s machine and changes the victim system’s network settings, allowing all outgoing connections to pass through a proxy.
According to CheckPoint researchers, “using those privileges, the malware will then install brew, a package manager for OS X, which will be used to install additional tools – TOR and SOCAT.”
DOK Deletes itself after Setting up Attacker’s Proxy
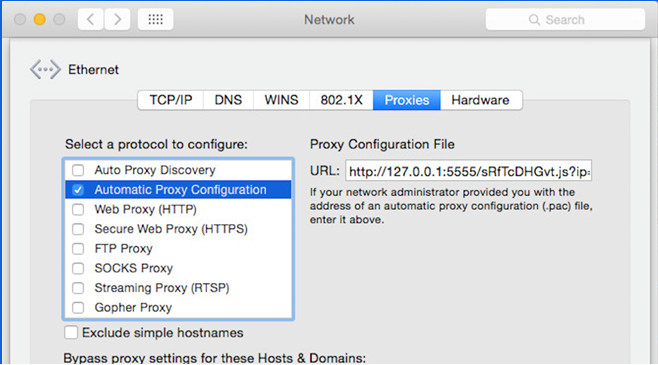
The malware then installs a new root certificate in the infected Mac, which allows the attacker to intercept the victim’s traffic using a man-in-the-middle (MiTM) attack.
“As a result of all of the above actions, when attempting to surf the web, the user’s web browser will first ask the attacker web page on TOR for proxy settings,” the researchers say.
“The user traffic is then redirected through a proxy controlled by the attacker, who carries out a Man-In-the-Middle attack and impersonates the various sites the user attempts to surf. The attacker is free to read the victim’s traffic and tamper with it in any way they please.”
According to researchers, almost no antivirus has updated its signature database to detect the DOK OS X malware, as the malware deletes itself once it modifies proxy settings on the target machines for interceptions.
Apple can resolve this issue just by revoking the developer certificate being abused by the malware author.
Meanwhile, users are always recommended to avoid clicking links contained in messages or emails from untrusted sources and always pay extra attention before proving your root password.