In the latest incident, the new variant of KillDisk ransomware has been found encrypting Linux machines, making them unbootable with data permanently lost.
W
KillDisk is the same component associated with the Black Energy malware that was used to hit several Ukrainian power stations in 2015, cutting power for thousands of people.
But according to ESET security researchers, the nasty KillDisk disk wiper malware is back with new variants that target Windows and Linux desktops and servers, encrypt files and then ask for an unusually large ransom:
Around $218,000 in Bitcoins – possibly the world’s most expensive ransom attacks.
What’s even Worst? Linux variant of the KillDisk ransomware does not store the encryption key anywhere on disk or command-and-control server.
So, even after you pay this extremely large ransom, you are not going to get any decryption key for recovery of your important files.
The good news is that ESET researchers have found a weakness in the encryption employed by the Linux variant which makes recovery of encrypted files possible, though difficult. But the same flaw doesn’t exist in the Windows variant of the KillDisk ransomware.
KillDisk Deletes your Files Even After Paying $218,000
According to researchers, the files of victims targeted with the Linux variant of the malware are encrypted using “Triple-DES applied to 4096-byte file blocks,” and each file on the computer is encrypted by a different set of 64-bit encryption keys.
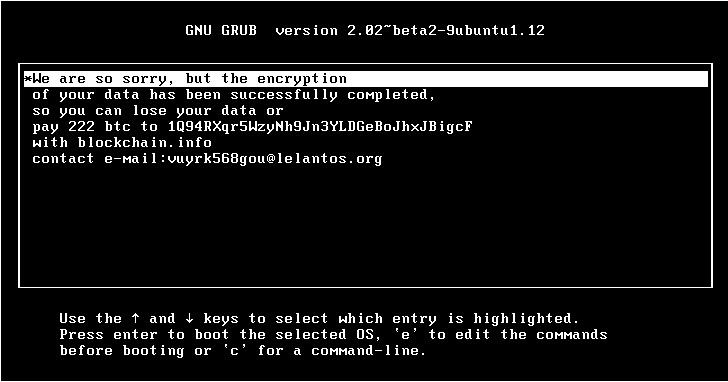
The malware then displays the ransom note in an unusual manner: within the GRUB bootloader, which means the KillDisk Linux ransomware overwrites the bootloader entries to show ransom text that asks victims to pay 222 Bitcoin.
But paying off the criminals ransom will not bring your files back, as the Linux variant does not store decryption keys anywhere.
KillDisk serves as another example of why paying ransom should not be considered an option. When dealing with criminals, there’s no guarantee of getting your data back – in this case, the criminals clearly never intended to deliver on their promises,” says Robert Lipovský, ESET Senior Researcher.
Prevention is the Best Practice
So, the only safe way of dealing with ransomware is prevention. As I previously recommended, the best defense against Ransomware is to create awareness within the organizations, as well as maintaining back-ups that are rotated regularly.
Most viruses are introduced by opening infected attachments or clicking on links to malware usually in spam emails. So, DO NOT CLICK on links provided in emails and attachments from unknown sources.
Moreover, ensure that your systems are running the latest version of Antivirus software with up to date malware definitions.